This website provides comprehensive information about secure systems. A secure system is a system with security mechanisms built into it. It can also be termed as secure cyber systems. In today’s world, no system is immune to security and other threats. Browser-based systems, including websites, are especially vulnerable to a constant onslaught of malicious attacks by hackers world-wide.
We cover many aspects of a secure system, starting from its concept to its development, maintenance, and modification. We include system models and modelling activities. We discuss various levels of secure systems starting from basic secure systems to a more advanced resilient system.
Secure and Resilient Systems Classification
A cyber system cannot expect security from outside in today’s ever-changing complex world of the Internet. It must be developed in such a way that it is “self-aware” of security and other threats and can protect itself and function securely. In fact, today’s cyber system should be a resilient cyber system. It should not be just self-protected but also, it should be self-optimizing, self-healing, self-configuring, self-managing, and self-adaptive. Figure 1 shows a classification hierarchy of secure and resilient systems.
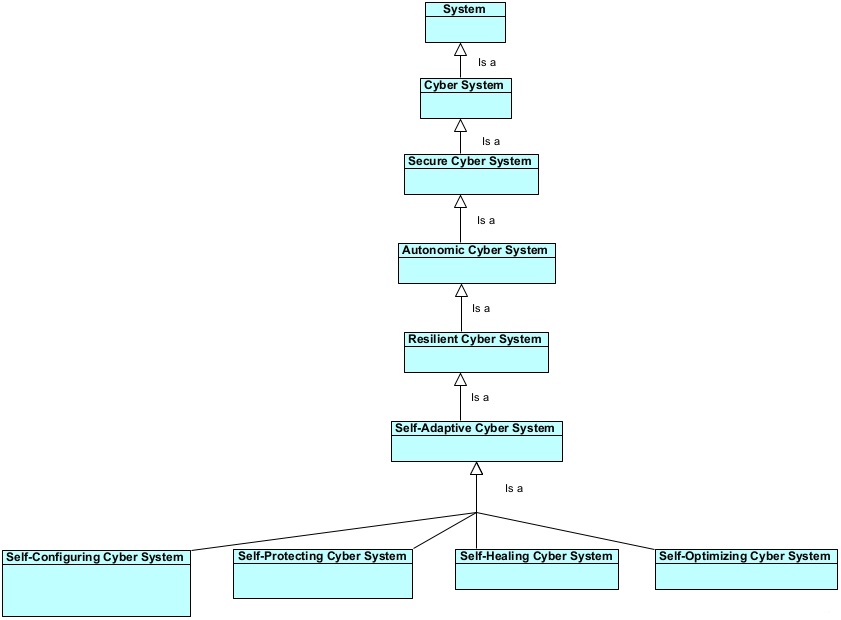
Figure 1.A Classification Hierarchy Showing Various Types of Systems.
The phrase “autonomic computing system was coined by IBM [59] inspired by the self-adaptive properties of autonomic nervous system of a human body. Autonomic cyber system in figure 1 refers to an autonomic computing system having a cyber component.
Self-Adaptive Cyber System
Self-adaptive systems self-adapt in response to changes in the self and in its environment [76], [77]. They make internal changes/adjustments to deal with the changed environment. They have self-managing capabilities.
Self-Configuring Cyber System
A self-configuring cyber system is capable of automatic reconfiguration of its parameters and components [77].
Self-Protecting Cyber System
A self-protecting cyber system can detect security threats and mitigate them [77].
Self-Healing Cyber System
A self-healing cyber system can discover, diagnose, and self-repair [77].
Self-Optimizing Cyber System
A self-optimizing cyber system can self-adjust and self-tune to optimize performance [77].
Resilient Cyber System
Today’s cyber systems are not only becoming complex, but they are also being subjected to a constant barrage of internal and external cyber as well as physical security threats. These complex cyber systems are generally an interconnected network of subsystems that integrate various kinds of software components, sometimes interfacing with equipment for sensing, data collection, and actuation capabilities. Examples are a website, an IOT, and a security camera system, etc. These systems tend to be a distributed system. A distributed system can be defined as a system whose components (i.e., software and hardware) may reside on different networked computers and these components coordinate their actions by communicating with each other through messages. In other words, the processing and data is distributed over many networked computers. Each component is responsible for its own processing and maintenance of data. The communication between these components is mostly asynchronous communication. Therefore, a centralized hierarchical control is inadequate to effectively protect and control even moderately large cyber systems. A hierarchical distributed control and coordination of a cyber system is emerging as a viable mechanism for its protection and operation. In fact, natural and man-made systems evolve into complex distributed adaptive systems that differentiate themselves into specialized units (i.e., components) with each unit doing its own task and making its own decision. For example, human body can be viewed as such a system. We propose to build this feature of differentiated and specialized self-adaptive units in our model of a resilient cyber system (RCS). A resilient cyber system is a cyber system (CS) that can protect and adapt itself appropriately in a changing environment. The changing environment includes internal and external security risks as well as component failures. This definition has been synthesized from several works on cyber physical system security and resilience [4]–[6], self-healing systems [7]–[10], and resilience in socio-ecological systems [11]. There is an increasing interest in modelling and designing a RCS as an interconnected system of self-contained components (i.e., devices) [4] with built-in control and self-adaptation [9]. A resilient cyber physical system (RCPS) [75] is a basically a subset of RCS. In a large RCS, such as an electric power system, each unit should be capable of self-protection and autonomous operation. Industry 4.0[12] and 2030 Vision for Industry 4.0[13] stipulates different levels of smart objects and factories that can inter-operate autonomously. This requires self-adaptation and intelligence in every unit/component that is a part of a hierarchical decentralized system. In other words, every unit must not only self-adapt but also protect itself from security and other attacks while interoperating together as part of a hierarchical decentralized system. To address this goal, we propose a novel modelling scheme to design a resilient cyber system whose components have built-in self-adaptation and self-protection.
This paper presents a resilient hierarchical distributed model of a cyber system (CS). The model is made up of hierarchically structured and interconnected self-contained resilient units (components/devices/software) each capable of self-protection and self-adaptation. The proposed resilient hierarchical distributed modelling scheme, henceforth called RDMS, enables us to build various levels of self-contained resilient units using lower-level units as building blocks to build the higher (upper) level units. We develop a comprehensive RDMS to integrate the security and resiliency features into each of the self-contained resilient units of CS. We model an electric power system as a resilient distributed cyber system to illustrate the development of a comprehensive resilient model.
RDMS consists of a basic set of semantic RCS schemes to build RCS units. A semantic RCPS schema is an integrated representation of four interrelated constituent components of a RCS—physical, cyber, connectional, and the resilient components. Each RCS unit is based upon the semantic RCS schema and has built-in requisite components to be resilient and protect itself from cyber and physical attacks. To the best of our knowledge, this is the first attempt to delineate the concept of an integrated self-sufficient unit in managing its physical, cyber, connectional, and resilient functions.
The article is organized as follows. The next section reviews the related extant research work. Section 3 discusses the resilient hierarchical distributed modelling scheme. Section 4 shows the application of RDMS in the domain of the electric power system. Section 5 presents a comparative evaluation of RDMS. The paper concludes with section 6 followed by the references.
Current Research on RCS Modelling and Design
The cross-cutting research work on CS and RCS covers many disciplines and views. NIST’s CPS framework [14], equally applicable to RCS, is a comprehensive reference framework suitable for discussing RCPS-related research covering many disciplines and views. The CPS framework is described in a great detail by the Cyber Physical Systems Public Working Group in a two-volume report [14], [15]. The CPS framework captures the generic CPS functionalities, activities, and artifacts needed to conceptualize, realize, and assure a CPS [14]. It consists of three elements—Domains, Facets, and Aspects. Domains refer to application domains such as manufacturing, energy, and transportation, etc. Facets are the components of the systems engineering process with associated activities and artifacts. A facet is a collection of activities that produce artifacts driven by aspects and their concerns for a CS. Aspects are groups of concerns. As an example, the trustworthiness aspect includes concerns such as security, privacy, safety, and resilience[14]. Research on RCS modelling and design can be discussed under the conceptualization of an assured CPS. The conceptualization facet consists of activities and artifacts that produce a model/architecture of RCS.
Literature on complex adaptive systems, sociotechnical systems, control systems, self-healing systems, autonomous computing, and contract-based design, etc. have contributed significantly to the methods and techniques for improving the architecture of a RCPS. There are several state-of-the-art research surveys [7], [16]–[23] dealing with different facets of a resilient cyber system—conceptualization, realization, and assurance in various areas and forms. Most of the RCS related research can be classified into the following categories:
- Security & Privacy
- Self-adaptation & Self-healing
- Framework and Architecture
- Design and Modelling
- Formal Methods, Analysis, and Algorithm
- Distributed Network Performance Analysis & Management
- Simulation and Simulation Platform.
CPS security & privacy research [21], [24]–[27] covers attacks, defences, privacy, and security risk assessment of interdependent cyber and physical systems. Self-healing can be considered as a specialized form of self-adaptive systems. Research on self-adaptation and self-healing [[7]–[10], [16], [18], [28], [28]–[33] covers self-adaptation mechanisms, methods, knowledgebases, and self-adaptive architecture, etc. CPS framework and architecture research [4], [14], [15], [17], [28], [34]–[39] covers CPS fundamentals and foundations, CPS framework and architecture, CPS metrics, and CPS maturity model, etc. CPS design and modelling research [1], [9, p.], [10], [30], [31], [40]–[42] covers design architecture, meta-model, method, and design model, etc. Formal methods, analysis, and algorithmic research [43]–[46] focuses on formal mathematical modelling, verification, and analysis of various CPS issues such as ascertaining run-time structure, behaviour, and non-functional properties. CPS distributed network performance analysis & management research [5], [47]–[50] has focused on modelling and analysis distributed network performance, assessment, and management. CPS simulation and simulation platform research [51]–[56] covers simulation platforms, simulation, and testbeds. Each of the above RCPS research areas are being investigated quite vigorously by several researchers. Obviously, it would be too peripheral an exercise to review every category of CPS-related research. Here, we limit our discussion of only those research works that have a direct relevance to our proposed work. There is a substantial research progress on several fronts addressing the design and modelling of a cyber physical system and its security. Cyber physical system security framework [4] provides a hierarchical approach for designing cyber physical system security (CPSS) and measuring its residual risk. The CPSS framework’s concept of a hierarchical CPS and a CPS being a “self-contained device” (i.e., self-contained unit) suggests building self-contained CPS units that are built of lower-level CPS units. This is a major work on emphasizing the use of self-contained CPS units. The literature on contract based design [5], [41], [57] discusses the advantages of contract-based design of CPS components. The contract-based design concepts enable us to create less dependency among CPS units. The CPS units are designed as per their specifications. Work on the contract-based design has contributed to the importance of formal specifications. The research work on self-adaptive and self-healing systems [7], [9], [16], [28], [29] discuss the concepts and techniques for achieving self-protection, self-healing, and self-configuration in each CPS unit. The work on self-adaptive systems has brought forth the concept of self-awareness, self-correction, context-awareness, and interaction-awareness in a system. The research works on control systems [20], [58] provide different kinds of architectures such as a distributed control for controlling and coordinating devices (units) within a CPS. Dynamic identification, assessment, and reconfiguration of distributed topology have been some of the major contributions from work on network and control systems. Morozov, Lezoche, and Panetto [1] use formal concept analysis (FCA) approach to model a large scale set of collaborative CPS. They present a meta-model to concretize the broad definition of cyber physical systems. This meta-model can be used to define cyber and physical components of a general CPS component with the proper inter-operability. We enhance the meta-model [1], [4] concepts and incorporate the additional concepts from CPSS, self-adaptation, distributed control, and contract-based design into a comprehensive distributed modelling scheme for structuring and designing resilient cyber physical systems.
Resilient Hierarchical Distributed Modelling Scheme (RDMS)
In this section, we discuss briefly the proposed novel RDMS to build a resilient hierarchical distributed model of cyber physical systems. Please see the reference [75] for a detailed discussion. RDMS, unlike the other extant schemes, builds security and resiliency features and functions into each RCS unit. As part of the resilient distributed modelling scheme, we develop:
- A concept of basic RCS.
- A meta model of RCS.
- A structure of an RCS unit.
- A method to build RCS units.
Basic Resilient Cyber System
A CS is variously defined to mean a complex adaptive system that uses physical, cyber, and connectional components to accomplish its goal. Here, we use the definition of CS “as electronics systems that operate as a single, self-contained device, or within an interconnected network providing shared operations with built-in resilient controls” [4]. This definition enables us to define an RCS at various levels of granularity. We introduce the concept of a basic RCS as the most elemental level of RCS. We extend the basic construct for representing a function object in the IDEF0 method ([73], [74]) to provide a comprehensive construct for an integrated definition of an RCS. The comprehensive construct is shown in figure 1. The box represents an RCS entity and arrows represent data related to the RCS entity. A RCS entity is a construct that can be used to embody a resilient CS. Each arrow represents a “pipeline” through which various types of data and material flow. As a general interpretation of figure 1, an RCS entity, under control, transforms or consumes input and produces output using mechanisms. Security risks are also viewed as input and risk mitigation techniques as mechanisms. The adaptation mechanism refers to tools, methods, and techniques to bring about the RCS entity’s adaptation. The other mechanism includes means, methods, and techniques used to conduct the activity of the entity. Control represents plan, pre-established parameters, etc. that act as constraints for the RCS entity. Knowledge source is shown explicitly as a special kind of control used by the RCS entity in achieving its resiliency. The term resilience is used here to imply protection and adaptation in a changing environment. The RCS entity can update its knowledge source based upon its experience with its environment. The updated knowledge source is available immediately for use by the RCS entity.
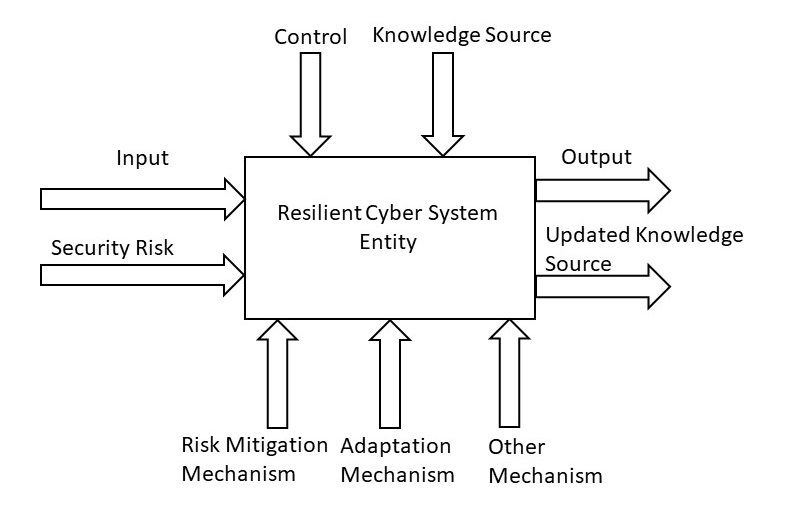
Figure 2. A comprehensive Construct for the Integrated Definition of an RCS Entity.
The basic construct of a RCS entity shown in figure 1 enables us to specify an integrated view of physical, cyber, connectional, and resilient components of a resilient cyber system. It makes the various aspects of an RCS entity more explicit. Figure 2 shows an abstract concept of a basic resilient cyber system entity in terms of its basic components. This entity reflects the specification of a resilient cyber physical system as shown in figure 1. The entity can process its inputs, outputs, and signals under the guidance of its knowledge source and, if needed, make the appropriate changes in its operation. Every higher-level RCS is based upon this basic RCS entity. Figure 2 also shows the structure of an RCS unit. We describe the RCS unit later in this section.
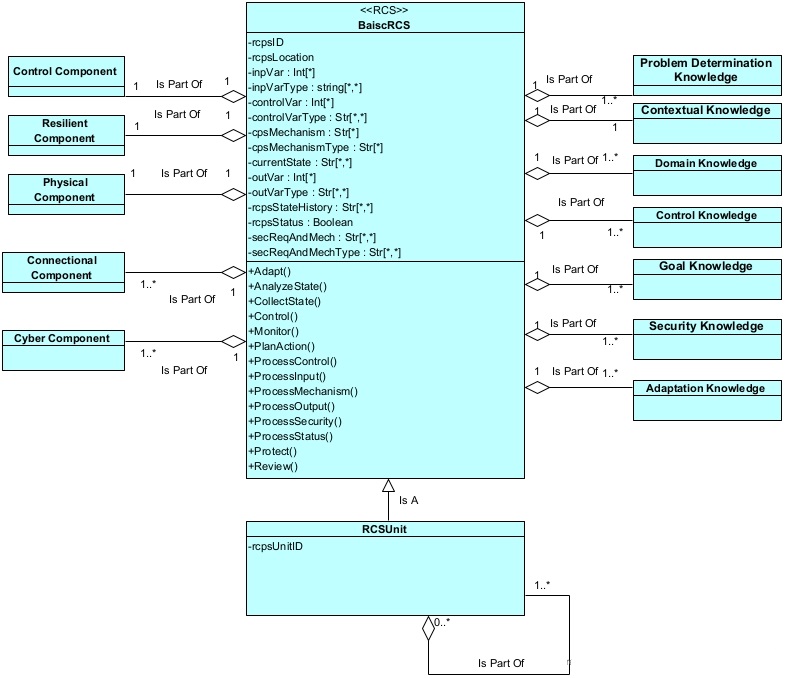
Figure 3. An UML class diagram showing the RCS meta model. It also shows the structure of a basic RCS Entity and RCS Unit. An RCS Unit is made up of one or more other RCS units and BasicRCS. BasicRCS is a concise term for the basic RCS Entity.
The basic RCS entity has a set of attributes and a set of operations (methods that work on the RCS unit) based upon the various RCS components shown in figure 2. Table 1 describes the attributes and operations of the basic RCS entity. The operations have been derived based upon the RCS’s basic construct and a synthesis of prior work on autonomic computing, self-adaptive systems, and robotics. It can process various types of inputs and controls and produce the appropriate outputs. It maintains a list of security requirements and the corresponding security mechanisms to mitigate security risks. It can assess the situation and act appropriately. Each RCS maintains a local knowledgebase containing various types of knowledge—context, domain, control, goal, security, adaptation, and problem determination knowledge [59] in addition to the RCS historical data. It also maintains data about its state allowing it to use a proactive resilient control strategy [58], [60].
Table 1. Description of Basic RCS entity’s attributes and Operations
An RCS unit is a BasicRCS and may contain other RCS units. An RCS unit is the major building block of higher level RCS units as shown in figure 2. Figure 2 shows the proposed RCS meta model relating a RCS unit to the basic RCS and to itself. This recursive definition of an RCS unit enables us to build a hierarchy of RCS units. Each RCS unit is self-contained and self-adaptive. This meta model will be discussed in the next section. Each RCS unit has its own knowledgebase. We discuss the various components of the knowledgebase next.
Knowledgebase of an RCS Unit
A knowledgebase of a RCS unit contains various types of information and data for the RCS unit to operate, monitor, control, protect, and adapt to changes in the system as well as the environment. An RCS can be viewed as a self-adaptive system. Several research works in self-adaptive systems and robotics have proposed and used a knowledgebase for adaptation. The nature of the knowledgebase of a self-adaptive system depends upon the complexity-level of the self-adaptive system. An IBM whitepaper [59] provides a comprehensive description of an autonomic computing system that has a built-in self-adaptiveness. The autonomic computing system has five major building blocks—Manageability endpoints, Knowledge sources, Autonomic managers, and Manual managers [59] that bring in the ability to self-adapt. An autonomic manager has four functions—Monitor, Analyse, Plan, and Execute (MAPE). These functions use various kinds of knowledge resources. The monitor, analyse, plan, execute, knowledge (MAPE-K) feedback loop has been used as a basic concept in self-managed systems. Based upon the MAPE-K Feedback Loop [59], an adaptive system should have four types of knowledge—knowledge about itself (Ksys), its environment (Kenv), its goal (Kgoal), and the adaption (Kadapt) [30]. We suggest that each RCS unit should maintain an appropriate level of Ksys, Kenv, Kgoal, and Kadapt. We expound these types of knowledge in terms of their content and possible structure.
All these knowledge types cover contextual knowledge, domain knowledge, problem determination knowledge, requirements/goal knowledge, and adaptation knowledge, etc. Specifically, we need the following kinds of information for a system to be resilient:
- Information about the various goals—performance, security, and adaptation requirements of an RCS unit.
- Information about the status of the RCS unit, its monitored data.
- Information about the various states and transitional actions of the RCS unit.
- Information about the RCS unit’s configuration, components, and their interconnections.
- Meta information about the RCS unit’s domain.
- Information about the security requirement and mechanism rules.
- Information about adaptation mechanism and rules.
Figure 4 shows a detailed breakdown of an RCPS unit’s knowledgebase.

Figure 4. Typical knowledge subcomponents of RCS Unit Knowledgebase
The various knowledge shown in figure 4 can be described using a combination of knowledge representation schemes such as hierarchical state machine [59], [60] , topology [61], [62], ontology [63], [64], and decision-rule [28].
A hierarchical state machine or a hierarchical state transition diagram is used to show/model all-possible states of a RCS unit, events that trigger transitions between states, and the transition actions. A hierarchical state machine is very effective in capturing the states and transitions of a hierarchical distributed RCS.
A hierarchical distributed RCS can be modelled/represented as a network of various levels of RCS units. The network structure is shown in the form a topology. The topology captures the information about the various component and their interconnection.
An ontology allows us to capture the semantics behind a domain knowledge.
In this article, we start with the analysis and design of secure systems. We discuss the analysis and design of resilient cyber systems in subsequent article.
References
[1] D. Morozov, M. Lezoche, and H. Panetto, “Multi-paradigm modelling of Cyber-Physical Systems,” IFAC-Pap., vol. 51, no. 11, pp. 1385–1390, 2018, doi: 10.1016/j.ifacol.2018.08.334.
[2] S. N. Bar-Joseph Ziv, “Distributed Information Processing in Biological and Computational Systems.” https://cacm.acm.org/magazines/2015/1/181614-distributed-information-processing-in-biological-and-computational-systems/fulltext (accessed Apr. 26, 2021).
[3] D. N. Fisher and J. N. Pruitt, “Insights from the study of complex systems for the ecology and evolution of animal populations,” Curr. Zool., vol. 66, no. 1, pp. 1–14, Feb. 2020, doi: 10.1093/cz/zoz016.
[4] D. DiMase, Z. A. Collier, K. Heffner, and I. Linkov, “Systems engineering framework for cyber physical security and resilience,” Environ. Syst. Decis., vol. 35, no. 2, pp. 291–300, Jun. 2015, doi: 10.1007/s10669-015-9540-y.
[5] M. S. Haque, D. Jun Xian Ng, A. Easwaran, and K. Thangamariappan, “Contract-Based Hierarchical Resilience Management for Cyber-Physical Systems,” Computer, vol. 51, no. 11, pp. 56–65, Nov. 2018, doi: 10.1109/MC.2018.2876071.
[6] R. Francis and B. Bekera, “A metric and frameworks for resilience analysis of engineered and infrastructure systems,” Reliab. Eng. Syst. Saf., vol. 121, pp. 90–103, Jan. 2014, doi: 10.1016/j.ress.2013.07.004.
[7] D. Ghosh, R. Sharman, H. Raghav Rao, and S. Upadhyaya, “Self-healing systems — survey and synthesis,” Decis. Support Syst., vol. 42, no. 4, pp. 2164–2185, Jan. 2007, doi: 10.1016/j.dss.2006.06.011.
[8] B. H. C. Cheng et al., “Software Engineering for Self-Adaptive Systems: A Research Roadmap,” in Software Engineering for Self-Adaptive Systems, vol. 5525, B. H. C. Cheng, R. de Lemos, H. Giese, P. Inverardi, and J. Magee, Eds. Berlin, Heidelberg: Springer Berlin Heidelberg, 2009, pp. 1–26.
[9] D. Ratasich, O. Hoftberger, H. Isakovic, M. Shafique, and R. Grosu, “A Self-Healing Framework for Building Resilient Cyber-Physical Systems,” in 2017 IEEE 20th International Symposium on Real-Time Distributed Computing (ISORC), Toronto, ON, Canada, May 2017, pp. 133–140, doi: 10.1109/ISORC.2017.7.
[10] D. Ratasich, T. Preindl, K. Selyunin, and R. Grosu, “Self-healing by property-guided structural adaptation,” in 2018 IEEE Industrial Cyber-Physical Systems (ICPS), St. Petersburg, May 2018, pp. 199–205, doi: 10.1109/ICPHYS.2018.8387659.
[11] C. Folke, “Resilience: The emergence of a perspective for social–ecological systems analyses,” Glob. Environ. Change, vol. 16, no. 3, pp. 253–267, Aug. 2006, doi: 10.1016/j.gloenvcha.2006.04.002.
[12] “What is Industrie 4.0?” https://www.plattform-i40.de/PI40/Navigation/EN/Industrie40/WhatIsIndustrie40/what-is-industrie40.html (accessed Nov. 03, 2020).
[13] “Position Paper 2030 Vision for Industrie 4.0.” https://www.plattform-i40.de/PI40/Redaktion/EN/Downloads/Publikation/Positionspapier%20Leitbild%20(EN).html (accessed Nov. 03, 2020).
[14] E. R. Griffor, C. Greer, D. A. Wollman, and M. J. Burns, “Framework for Cyber-Physical Systems: Volume 1, Overview,” NIST, vol. 1, no. 1, pp. 1–79, Jun. 2017.
[15] E. R. Griffor, C. Greer, D. A. Wollman, and M. J. Burns, “Framework for Cyber-Physical Systems: Volume 2, Working Group Reports,” NIST, vol. 2, no. 1, pp. 1–163, Jun. 2017.
[16] D. Weyns, “Software Engineering of Self-Adaptive Systems: An Organised Tour and Future Challenges,” Berl. Ger. Springer, p. 43, 2017.
[17] J. Moura and D. Hutchison, “Cyber-Physical Systems Resilience: State of the Art, Research Issues and Future Trends,” ArXiv160301650 Cs Math, p. 42, 2019.
[18] H. Muccini, M. Sharaf, and D. Weyns, “Self-Adaptation for Cyber-Physical Systems: A Systematic Literature Review,” in 2016 IEEE/ACM 11th International Symposium on Software Engineering for Adaptive and Self-Managing Systems (SEAMS), May 2016, pp. 75–81, doi: 10.1109/SEAMS.2016.016.
[19] A. Bennaceur et al., “Modelling and Analysing Resilient Cyber-Physical Systems,” Montréal, Canada, May 2019, Accessed: Feb. 24, 2020. [Online]. Available: https://hal.archives-ouvertes.fr/hal-02104308.
[20] R. Scattolini, “Architectures for distributed and hierarchical Model Predictive Control – A review,” J. Process Control, vol. 19, no. 5, pp. 723–731, May 2009, doi: 10.1016/j.jprocont.2009.02.003.
[21] J. Giraldo, E. Sarkar, A. A. Cardenas, M. Maniatakos, and M. Kantarcioglu, “Security and Privacy in Cyber-Physical Systems: A Survey of Surveys,” IEEE Des. Test, vol. 34, no. 4, pp. 7–17, Aug. 2017, doi: 10.1109/MDAT.2017.2709310.
[22] J. Zeng, L. T. Yang, M. Lin, H. Ning, and J. Ma, “A survey: Cyber-physical-social systems and their system-level design methodology,” Future Gener. Comput. Syst., vol. 105, pp. 1028–1042, Apr. 2020, doi: 10.1016/j.future.2016.06.034.
[23] S. K. Khaitan and J. D. McCalley, “Design Techniques and Applications of Cyberphysical Systems: A Survey,” IEEE Syst. J., vol. 9, no. 2, pp. 350–365, Jun. 2015, doi: 10.1109/JSYST.2014.2322503.
[24] R. Alguliyev, Y. Imamverdiyev, and L. Sukhostat, “Cyber-physical systems and their security issues,” Comput. Ind., vol. 100, pp. 212–223, Sep. 2018, doi: 10.1016/j.compind.2018.04.017.
[25] G. A. Fink, T. W. Edgar, T. R. Rice, D. G. MacDonald, and C. E. Crawford, “Chapter 9 – Security and Privacy in Cyber-Physical Systems*,” in Cyber-Physical Systems, H. Song, D. B. Rawat, S. Jeschke, and C. Brecher, Eds. Boston: Academic Press, 2017, pp. 129–141.
[26] H. I. Kure, S. Islam, and M. A. Razzaque, “An Integrated Cyber Security Risk Management Approach for a Cyber-Physical System,” Appl. Sci., vol. 8, no. 6, Art. no. 6, Jun. 2018, doi: 10.3390/app8060898.
[27] W. Wu, R. Kang, and Z. Li, “Risk assessment method for cyber security of cyber physical systems,” in 2015 First International Conference on Reliability Systems Engineering (ICRSE), Oct. 2015, pp. 1–5, doi: 10.1109/ICRSE.2015.7366430.
[28] Y. Brun et al., “Engineering Self-Adaptive Systems through Feedback Loops,” in Software Engineering for Self-Adaptive Systems, B. H. C. Cheng, R. de Lemos, H. Giese, P. Inverardi, and J. Magee, Eds. Berlin, Heidelberg: Springer Berlin Heidelberg, 2009, pp. 48–70.
[29] S. S. Laster, “Autonomic Computing: Towards a Self-Healing System,” p. 17, 2007.
[30] V. Klös, T. Göthel, and S. Glesner, “Adaptive Knowledge Bases in Self-Adaptive System Design,” in 2015 41st Euromicro Conference on Software Engineering and Advanced Applications, Aug. 2015, pp. 472–478, doi: 10.1109/SEAA.2015.48.
[31] D. G. D. L. Iglesia and D. Weyns, “MAPE-K Formal Templates to Rigorously Design Behaviors for Self-Adaptive Systems,” ACM Trans. Auton. Adapt. Syst. TAAS, vol. 10, no. 3, p. 15:1-15:31, Sep. 2015, doi: 10.1145/2724719.
[32] M. Pelc and D. Galus, “Adaptation Architecture for Self-Healing Computer Systems,” Int. J. Softw. Eng. Knowl. Eng., vol. 27, no. 05, pp. 791–815, Jun. 2017, doi: 10.1142/S0218194017500292.
[33] A. J. Ramirez and B. H. C. Cheng, “Design patterns for developing dynamically adaptive systems,” in Proceedings of the 2010 ICSE Workshop on Software Engineering for Adaptive and Self-Managing Systems, Cape Town, South Africa, May 2010, pp. 49–58, doi: 10.1145/1808984.1808990.
[34] J. Lee, B. Bagheri, and H.-A. Kao, “A Cyber-Physical Systems architecture for Industry 4.0-based manufacturing systems,” Manuf. Lett., vol. 3, pp. 18–23, Jan. 2015, doi: 10.1016/j.mfglet.2014.12.001.
[35] S. K. Khaitan, J. D. McCalley, and C. C. Liu, Eds., Cyber Physical Systems Approach to Smart Electric Power Grid. Berlin Heidelberg: Springer-Verlag, 2015.
[36] J. Jamaludin and J. M. Rohani, “Cyber-Physical System (CPS): State of the Art,” in 2018 International Conference on Computing, Electronic and Electrical Engineering (ICE Cube), Nov. 2018, pp. 1–5, doi: 10.1109/ICECUBE.2018.8610996.
[37] M. A. Haque, G. K. De Teyou, S. Shetty, and B. Krishnappa, “Cyber Resilience Framework for Industrial Control Systems: Concepts, Metrics, and Insights,” in 2018 IEEE International Conference on Intelligence and Security Informatics (ISI), Nov. 2018, pp. 25–30, doi: 10.1109/ISI.2018.8587398.
[38] M. A. Haque, S. Shetty, and B. Krishnappa, “Cyber-Physical System Resilience,” in Complexity Challenges in Cyber Physical Systems, John Wiley & Sons, Ltd, 2019, pp. 301–337.
[39] J. C. Strassner, N. Agoulmine, and E. Lehtihet, “FOCALE – A Novel Autonomic Networking Architecture,” Int. Trans. Syst. Sci. Appl. J., vol. 3, no. 1, pp. 64–79, May 2007.
[40] J. Lin, S. Sedigh, and A. Miller, “A Semantic Agent Framework for Cyber-Physical Systems,” in Semantic Agent Systems: Foundations and Applications, A. Elçi, M. T. Koné, and M. A. Orgun, Eds. Berlin, Heidelberg: Springer, 2011, pp. 189–213.
[41] A. Sangiovanni-Vincentelli, W. Damm, and R. Passerone, “Taming Dr. Frankenstein: Contract-Based Design for Cyber-Physical Systems*,” Eur. J. Control, vol. 18, no. 3, pp. 217–238, Jan. 2012, doi: 10.3166/ejc.18.217-238.
[42] P. Nuzzo, J. B. Finn, A. Iannopollo, and A. L. Sangiovanni-Vincentelli, “Contract-based design of control protocols for safety-critical cyber-physical systems,” in 2014 Design, Automation Test in Europe Conference Exhibition (DATE), Mar. 2014, pp. 1–4, doi: 10.7873/DATE.2014.072.
[43] S. Bistarelli, F. Martinelli, I. Matteucci, and F. Santini, “A Formal and Run-Time Framework for the Adaptation of Local Behaviours to Match a Global Property,” in Formal Aspects of Component Software, Cham, 2017, pp. 134–152, doi: 10.1007/978-3-319-57666-4_9.
[44] D. Du, P. Huang, K. Jiang, F. Mallet, and M. Yang, “MARTE/pCCSL: Modeling and Refining Stochastic Behaviors of CPSs with Probabilistic Logical Clocks,” in Formal Aspects of Component Software, Cham, 2017, pp. 111–133, doi: 10.1007/978-3-319-57666-4_8.
[45] Z. Yu, J. Ouyang, S. Li, and X. Peng, “Formal modeling and control of cyber-physical manufacturing systems:,” Adv. Mech. Eng., Oct. 2017, doi: 10.1177/1687814017725472.
[46] H. Giese, “Formal Models and Analysis for Self-adaptive Cyber-physical Systems,” in Formal Aspects of Component Software, Cham, 2017, pp. 3–9, doi: 10.1007/978-3-319-57666-4_1.
[47] H.-D. Tran, L. V. Nguyen, P. Musau, W. Xiang, and T. T. Johnson, “Real-Time Verification for Distributed Cyber-Physical Systems,” ArXiv190909087 Cs, Sep. 2019, Accessed: Feb. 28, 2020. [Online]. Available: http://arxiv.org/abs/1909.09087.
[48] S. Xia et al., “Distributed State Estimation of Multi-region Power System based on Consensus Theory,” Energies, vol. 12, no. 5, Art. no. 5, Jan. 2019, doi: 10.3390/en12050900.
[49] S. Adepu et al., “Control Behavior Integrity for Distributed Cyber-Physical Systems,” ArXiv181208310 Cs, Dec. 2018, Accessed: Feb. 28, 2020. [Online]. Available: http://arxiv.org/abs/1812.08310.
[50] I. Akkaya, Y. Liu, and E. A. Lee, “Modeling and Simulation of Network Aspects for Distributed Cyber-Physical Energy Systems,” in Cyber Physical Systems Approach to Smart Electric Power Grid, S. K. Khaitan, J. D. McCalley, and C. C. Liu, Eds. Berlin, Heidelberg: Springer Berlin Heidelberg, 2015, pp. 1–23.
[51] A. T. Al-Hammouri, “A comprehensive co-simulation platform for cyber-physical systems,” Comput. Commun., vol. 36, no. 1, pp. 8–19, Dec. 2012, doi: 10.1016/j.comcom.2012.01.003.
[52] H. Neema, J. Sztipanovits, C. Steinbrink, T. Raub, B. Cornelsen, and S. Lehnhoff, “Simulation integration platforms for cyber-physical systems,” in Proceedings of the Workshop on Design Automation for CPS and IoT, Montreal, Quebec, Canada, Apr. 2019, pp. 10–19, doi: 10.1145/3313151.3313169.
[53] M. H. Cintuglu, O. A. Mohammed, K. Akkaya, and A. S. Uluagac, “A Survey on Smart Grid Cyber-Physical System Testbeds,” IEEE Commun. Surv. Tutor., vol. 19, no. 1, pp. 446–464, 2017, doi: 10.1109/COMST.2016.2627399.
[54] T. Roth and M. Burns, “A gateway to easily integrate simulation platforms for co-simulation of cyber-physical systems,” in 2018 Workshop on Modeling and Simulation of Cyber-Physical Energy Systems (MSCPES), Apr. 2018, pp. 1–6, doi: 10.1109/MSCPES.2018.8405394.
[55] OpenSim, “COSSIM – Cyber-Physical Systems (CPS) Simulator Framework,” omnetpp.org/download-items/COSSIM.HTML, 2018. https://omnetpp.org/download-items/COSSIM.html (accessed Feb. 27, 2020).
[56] E. Kremers, P. Viejo, O. Barambones, and J. G. de Durana, “A Complex Systems Modelling Approach for Decentralised Simulation of Electrical Microgrids,” in 2010 15th IEEE International Conference on Engineering of Complex Computer Systems, Mar. 2010, pp. 302–311, doi: 10.1109/ICECCS.2010.1.
[57] P. Derler, E. A. Lee, S. Tripakis, and M. Törngren, “Cyber-physical system design contracts,” in Proceedings of the ACM/IEEE 4th International Conference on Cyber-Physical Systems – ICCPS ’13, Philadelphia, Pennsylvania, 2013, p. 109, doi: 10.1145/2502524.2502540.
[58] C. G. Rieger, “Resilient control systems Practical metrics basis for defining mission impact,” in 2014 7th International Symposium on Resilient Control Systems (ISRCS), Denver, CO, USA, Aug. 2014, pp. 1–10, doi: 10.1109/ISRCS.2014.6900108.
[59] IBM, An architectural blueprint for autonomic computing, Fourth Edition. IBM Corporation, 2006.
[60] Y. Yang and R. Sydnor, “Resilient Control for Critical Infrastructures and Systems.,” in Nuclear Plant Instrumentation, Controls, and Human Machine Interface Technology, San diego, CA, Dec. 2011, p. 12.
[61] M. Yannakakis, “Hierarchical State Machines,” in Theoretical Computer Science: Exploring New Frontiers of Theoretical Informatics, Berlin, Heidelberg, 2000, pp. 315–330, doi: 10.1007/3-540-44929-9_24.
[62] D. Harel, “Statecharts: A visual formalism for complex systems,” Sci. Comput. Program., vol. 8, no. 3, pp. 231–274, Jun. 1987, doi: 10.1016/0167-6423(87)90035-9.
[63] P. Hines, S. Blumsack, E. C. Sanchez, and C. Barrows, “The Topological and Electrical Structure of Power Grids,” in 2010 43rd Hawaii International Conference on System Sciences, Jan. 2010, pp. 1–10, doi: 10.1109/HICSS.2010.398.
[64] E. Ozkan-Canbolat and A. Beraha, “Configuration and innovation related network topology,” J. Innov. Knowl., vol. 1, no. 2, pp. 91–98, Aug. 2016.
[65] C. Hildebrandt, S. Törsleff, B. Caesar, and A. Fay, “Ontology Building for Cyber-Physical Systems: A domain expert-centric approach,” in 2018 IEEE 14th International Conference on Automation Science and Engineering (CASE), Aug. 2018, pp. 1079–1086, doi: 10.1109/COASE.2018.8560465.
[66] J. Strassner, “Chapter 11 – Knowledge Representation, Processing, and Governance in the FOCALE Autonomic Architecture,” in Autonomic Network Management Principles, N. Agoulmine, Ed. Oxford: Academic Press, 2011, pp. 253–274.
[67] L. H. Fink and K. Carlsen, “Operating under stress and strain [electrical power systems control under emergency conditions],” IEEE Spectr., vol. 15, no. 3, pp. 48–53, Mar. 1978, doi: 10.1109/MSPEC.1978.6369445.
[68] A. Abur and A. G. Expósito, Power System State Estimation: Theory and Implementation. CRC Press, 2004.
[69] A. S. Mahima, “A Cyber-Physical Systems Approach to Water Distribution System Monitoring,” Thesis, 2015.
[70] Y. Wei and S. Li, “Water supply networks as cyber-physical systems and controllability analysis,” IEEECAA J. Autom. Sin., vol. 2, no. 3, pp. 313–319, Jul. 2015, doi: 10.1109/JAS.2015.7152666.
[71] B. Paithankar, Y.G. S. R., Fundamentals of Power System Protection, 1st ed. New Delhi: Prentice Hall of India, 2003.
[72] A. von Meier, Electric power systems: a conceptual introduction. Hoboken, N.J: IEEE Press : Wiley-Interscience, 2006.
[73] Lambert, J.H., Jennings, R.K. and Joshi, N.N. (2006), Integration of risk identification with business process models. Syst. Engin., 9: 187-198. https://doi.org/10.1002/sys.20054
[74] Bravoco, R.R., & Yadav, S.B. (1985). A methodology to model the functional structure of an organization. Computers in Industry, 6, 345-361.
[75] Surya B Yadav (2023) A resilient hierarchical distributed model of a cyber physical system, Cyber-Physical Systems, 9:2, 97-121, DOI: 10.1080/23335777.2021.1964101
[76] Mazeiar Salehie and Ladan Tahvildari. 2009. Self-adaptive software: Landscape and research challenges. ACM Trans. Auton. Adapt. Syst. 4, 2, Article 14 (May 2009), 42 pages. https://doi.org/10.1145/1516533.1516538
[77] Laddaga, R. 1997. Self-adaptive software. Tech. Rep. 98-12, DARPA BAA.
